HIPAA-compliant analytics and data activation platform: Effective and secure healthcare marketing
Discover marketing insights to securely optimize digital patient experience and maximize the impact of your campaigns. Analyze patient interactions, activate behavioral data, and grow revenue while keeping your health data protected.
Modules:
Analytics
Tag Manager
Data Activation
Consent Manager








Get effective healthcare marketing and full HIPAA compliance
Focus on your core business activities without worrying about HIPAA violations or loss of patient trust. Maintain full control and protect personal health information (PHI) with a business associate agreement (BAA) tailored to your needs.
Learn what drives your ROI and make smarter marketing decisions
Access complete, real-time patient data and confidently attribute traffic and conversions. Get precise insights into campaign effectiveness and understand where to allocate your marketing budget.
Transform real patient data into marketing actions that convert
Go beyond analysis and turn behavioral data into a powerful tool for improving user engagement. Run effective, privacy-compliant campaigns – encourage appointment scheduling, send reminders, and provide personalized recommendations.
Prioritize patient privacy without compromising marketing results
Collect valuable data and move securely within a HIPAA-compliant, audit-ready platform. Meet privacy obligations with safe US-based hosting, data encryption, granular access controls and advanced data anonymization.
Easily connect your existing marketing and data stack
Combine analytics, tag and consent management, and data activation within one scalable platform. Seamlessly integrate CRMs, BI and visualization tools and ad platforms to continue using Google Ads, Facebook Ads, Hubspot and others without risking compliance.
What you can do with Piwik PRO
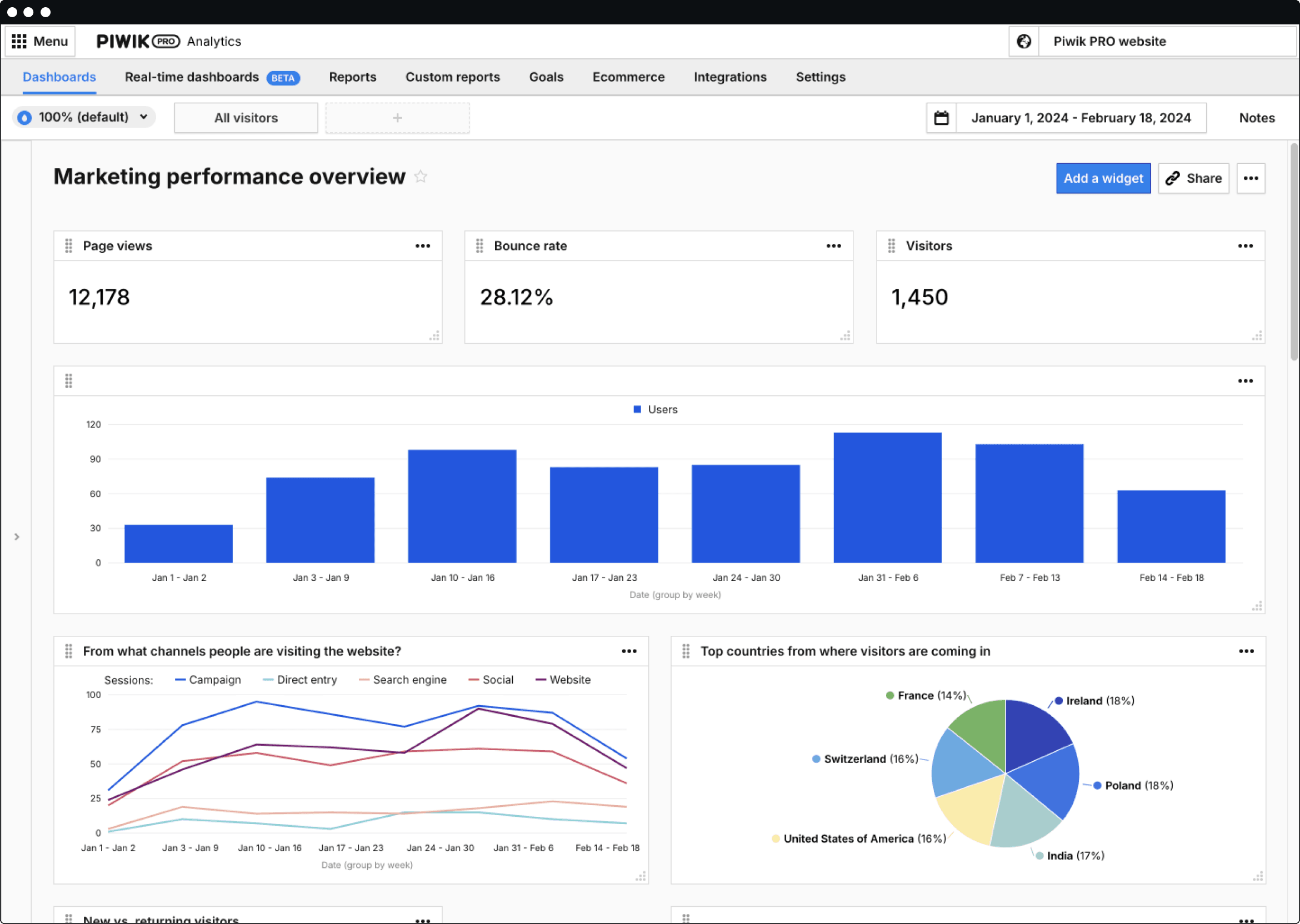
Get accurate traffic & conversion analytics
Know exactly where your visitors are coming from and improve their experience on your website while staying HIPAA-compliant. Use real-time dashboards, funnel analysis and user flow reports to identify drop-off points and optimize conversion paths.
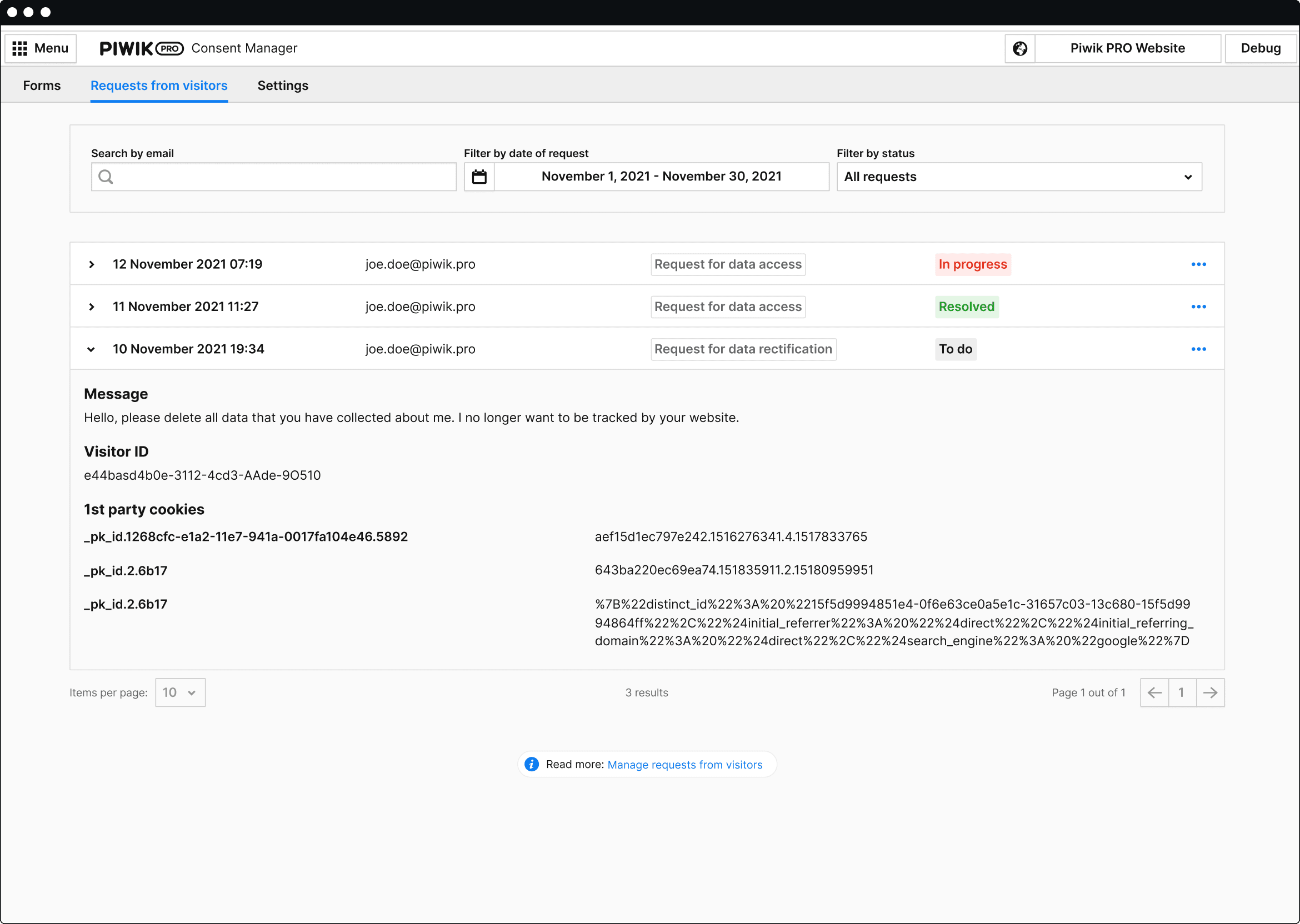
Ensure patient privacy & data security
Keep your patient data secure in an audit-ready infrastructure that offers encryption, US-based hosting and built-in privacy features. Safely integrate analytics with CRMs, BI tools, marketing automation platforms, EHR systems and other tools without risking compliance.
Better control over marketing tools
Use an all-in-one platform that signs a BAA and lets you control what tools you share the data with. Gain greater flexibility in making your analytics setup HIPAA-compliant with our Tag Manager. Adjust tag behavior to fit any data collection approach.

Improve patient acquisition & engagement
Build behavioral audiences based on the services users explore, how they schedule appointments, and what content they engage with. Create personalized experiences and drive user engagement via email, mobile app, or website pop-ups.

Reliable server-side data collection
Get greater control and flexibility in your setup and enhance data privacy with server-side tagging. Choose between server-side Google Tag Manager, Jentis, Stape, or TAGGRS. Improve data accuracy and collect data safely.
Success Story
Rochester Regional Health boosts its campaign and content performance with HIPAA-compliant insights gathered with Piwik PRO
“Piwik PRO felt familiar with both the UI and metrics. It has a low learning curve due to its similarity to Google Analytics, and we wanted to continue tracking all of the information we historically wished to capture in a HIPAA-compliant and easy way. We considered the price point, familiarity, capabilities, and functionality. The combination of all these factors led us to choose Piwik PRO. There wasn’t any other option on the market that allowed us to capture all the data we wanted and ensure it was HIPAA-compliant.”
Tyler Pierce
Manager, Digital Engagement at Rochester Regional Health
Piwik PRO analytics for healthcare in practice
Enhance marketing effectiveness
Measure the success of outreach initiatives, such as health awareness campaigns or patient education programs, and adjust strategies to drive stronger results.
Elevate patient engagement with data activation
Personalize patient experiences and deliver meaningful recommendations using a customer data platform for targeted email campaigns and on-site personalization.
Improve the ROI of your ad campaigns
Gain deeper insights into the performance of your Google Ads and other platforms, and activate actionable data directly – all while ensuring the protection of sensitive health information.
Improve SEO
Boost your website’s visibility by identifying trending topics and high-traffic keywords. Optimize content to improve search rankings and meet patient expectations, driving more traffic to your site.
Understand patients and their needs
Gain a holistic view of every digital touchpoint your patients encounter. Analyze user flow and funnel data to understand traffic sources through your website, social media, or email campaigns.
Optimize conversion rates
Streamline the patient journey from scheduling to service. Send conversion data like GCLID to refine targeting and boost performance.

How to make your analytics HIPAA-compliant: A practical checklist for healthcare marketers
Follow this step-by-step HIPAA compliance checklist to ensure your analytics meet healthcare privacy standards and protect patient data.
How Piwik PRO keeps you aligned with HIPAA
Customizable BAA
Partner with us to enhance your healthcare marketing efforts with a BAA adjusted to your needs, regardless of your chosen hosting option. Ensure joint compliance and liability for the services provided and establish clear responsibilities for PHI/ePHI.
Tailored compliance features
Piwik PRO offers HIPAA-compliant analytics with 256-bit AES encryption for ePHI and comprehensive audit logs to track user activity. These features protect patient data while providing valuable insights, enhancing accountability and building customer trust.
HIPAA certified
Piwik PRO has passed a comprehensive HIPAA-compliance analytics assessment as part of our SOC-2 Type II audit. Safeguard your patients’ sensitive health data with confidence, knowing you’re working with a vendor that meets the highest security standards.
Anonymization options
Disable the collection of IP addresses and other identifiers. Reduce the risk of exposing PHI and ensure no location data is inadvertently collected. Protect patient privacy and focus on broad demographic trends without compromising sensitive information.
100% data control
Be the sole controller of granular visitor information and access it at any time. Decide what ePHI you collect and how you use it to provide the best patient experience. We never use your data for any purpose other than what you agreed to, and we never share it with third parties.
Secure backup storage and hosting
Use safe backup solutions that replicate sensitive data to HIPAA-compliant Microsoft Azure data centers. Support consistent marketing efforts with backup options in the US cloud or 60+ private cloud locations.
Success Story
Shepherd Center increased patient referrals by 40% with Piwik PRO as their HIPAA-compliant analytics platform
“As part of our marketing objectives to drive patient referrals, we partnered with Piwik PRO to gain valuable insights into the user experience on our referral web pages and the referral process. After enhancing our on-page content, we saw a remarkable 215% increase in page views and a 79% drop in bounce rates, resulting in a 40% rise in online referrals. We have created more engaging content that is easier to navigate, making our website a better patient-centered referral experience.”
Kelsey Harris
Web Strategist at Shepherd Center
Resources on HIPAA-compliant analytics
We’ve gathered our content on HIPAA to help you evaluate your organization’s compliance and understand the requirements to comply with the law. Learn how to collect and process patient data online, what security measures to apply across your organization and tech, and how to find a HIPAA-compliant analytics vendor.
-
4 ways to make your analytics HIPAA-compliant: Implementation guide
Healthcare organizations have four main approaches to achieving HIPAA-compliant analytics. Each has different trade-offs in cost, technical complexity, and analytics capabilities. This guide compares all four implementation methods – from using Google Analytics with workarounds to deploying fully HIPAA-compliant analytics platforms – so you can choose the right approach for your organization’s needs and resources.
-
Is Google Analytics HIPAA-compliant?
If you use Google Analytics or similar software, you’re likely already optimizing your website to serve your customers better. But what about Google Analytics and HIPAA compliance? In short – if you’re a HIPAA-covered entity, using GA4 puts you at serious risk of a HIPAA breach. Google states that Google Analytics doesn’t satisfy HIPAA requirements. And…
-
HIPAA-compliant marketing & advertising: How to run compliant campaigns in healthcare
Healthcare organizations deal with tons of sensitive information concerning people’s health. It needs to be handled with proper care. In the US, safe parameters for using this kind of data in different contexts, including marketing, are set by HIPAA. Unfortunately, many companies are still unaware of the provisions of the law and the potential consequences…
-
PHI vs PII in HIPAA: Healthcare marketing compliance guide
Personally identifiable information (PII) and protected health information (PHI) may seem similar. However, there are critical distinctions between the two. While PII is a catch-all term for any information that can be associated with an individual, PHI applies specifically to HIPAA-covered entities dealing with identifiable patient information. Keeping HIPAA compliant and protecting patient information requires…
-
A review of HIPAA-compliant analytics platforms
As a healthcare organization subject to HIPAA, you’re walking a fine line when trying to improve the patient experience and ensure your activities are HIPAA-compliant. Vendors have been adjusting to the shifting privacy-oriented analytics landscape and their clients’ expectations. Many of them change their offers accordingly. At the same time, the dominant analytics vendors are…
-
The AHA’s lawsuit against HHS guidance on online tracking technologies: What it means for HIPAA-covered entities and their use of analytics
On June 20, 2024, a US district court ruled in favor of the American Hospital Association’s (AHA) lawsuit against the Department of Health and Human Services (HHS) bulletin on using online tracking technologies, declaring it beyond agency authority. The 2022 bulletin sought to inform entities regulated under HIPAA of their obligations concerning the use of…
FAQ
Who must follow HIPAA requirements?
The HIPAA rules apply to any individual or organization that meets the definition of a covered entity as stated in HIPAA guidelines.
Covered entities include:
- Health plans – for example, health insurance companies, HMOs, company health plans, and certain government programs that pay for health care, such as Medicare and Medicaid.
- Healthcare providers that conduct certain business electronically, such as electronically billing your health insurance – including most doctors, clinics, hospitals, psychologists, chiropractors, nursing homes, pharmacies, and dentists.
- Health care clearinghouses – entities that process nonstandard health information they receive from another entity into a standard (i.e., standard electronic format or data content), or vice versa.
Beyond covered entities, the following must adhere to HIPAA:
- Business associates
- Subcontractors
- Hybrid entities
- Researchers
A business associate can be an individual or company that provides services to a HIPAA-covered entity that requires them to have access to, store, use, or transmit protected health information. Generally, an analytics vendor will be a business associate.
What is PHI and its electronic version (called ePHI) under HIPAA?
PHI and ePHI is a subset of personally identifiable information (PII) that refers explicitly to information processed by HIPAA-covered entities. When health information is combined with a personal identifier, the data becomes PHI.
Examples of health information include:
- Medical test results
- Prescription or treatment records
- Billing information
- Appointment scheduling information
When health information is combined with a personal identifier, the data becomes PHI.
The Department of Health and Human Services (HHS) lists the 18 HIPAA identifiers:
- Name
- All geographic subdivisions smaller than a state (street address, city, county, zip code)
- Dates, including birthdate, admission date, discharge date, and date of death
- Telephone number
- Fax number
- Email address
- Social Security number
- Medical record number
- Health plan beneficiary numbers
- Account number
- Certificate/license number
- Vehicle identifiers and serial numbers, including license plate number
- Device identifiers and serial numbers
- Web URL
- IP address
- Biometric identifiers, including fingerprints and voice
- Full face photo
- Any other unique identifying number, characteristic, or code
This means that not all health information acquired by organizations is considered PHI. For example, phone numbers and residential addresses alone are not PHI. But this data will be considered PHI if it includes health information about an individual’s condition, the treatment of that condition, or the payment for the treatment. It also must be transmitted and maintained in any form by a covered entity.
Specific examples of PHI and ePHI include:
- Information your doctors, nurses, and other health care providers put in your medical record.
- Conversations your doctor has about your care or treatment with nurses and others.
- Information about you in your health insurer’s computer system.
- Billing information about you at your clinic.
Importantly, PII collected on a covered entity’s website or app is considered PHI even if the individual does not have an existing relationship with the entity or the PII does not include specific treatment or billing information. When a covered entity collects such information, it is indicative that the individual has received or will receive health care services or benefits from it.
Why is HIPAA compliance important?
HIPAA introduced several benefits for the healthcare industry to help transition from paper records to electronic copies of health information. HIPAA has helped to streamline administrative healthcare functions, improve efficiency in the healthcare industry, and ensure that protected health information is shared securely.
People now care about the privacy of their data more than ever. Health information is a special category of personal information because it contains details about users’ conditions that they may not want to disclose. Protecting the privacy of health-related data helps you maintain the trust of individuals whose information you are processing.
Neglecting users’ rights related to HIPAA can negatively affect your business and have a long-lasting impact on how patients view your organization. Since HIPAA is a standard that must be followed by many organizations similar to yours, the lack of compliance can make you lose business to your compliant competitors. Not to mention that any covered entity that violates HIPAA regulations can face civil action lawsuits, criminal charges, and hefty monetary penalties.
How can you stay compliant with HIPAA?
HIPAA makes covered entities responsible for complying with a number of rules – the Privacy Rule, Security Rule, Breach Notification Rule, Enforcement Rule, and Omnibus Rule. The first three rules are particularly important.
The Privacy Rule provides federal standards to protect the privacy of PHI – particularly, it:
- Limits how covered entities may use and disclose individually identifiable health information they receive or create.
- Gives individuals rights concerning their protected health information, including a right to review and obtain a copy of their medical records and the right to ask covered entities to amend the information if it is inaccurate or incomplete.
- Imposes administrative requirements for covered entities, such as training of employees concerning the Privacy Rule.
- Establishes civil penalties.
The Security Rule requires covered entities to maintain reasonable and appropriate administrative, technical, and physical safeguards to protect ePHI. Specifically, they must:
- Ensure the confidentiality, integrity, and availability of all e-PHI they create, receive, maintain, or transmit.
- Identify and protect against reasonably anticipated threats to the security or integrity of the information.
- Protect against reasonably anticipated, impermissible uses or disclosures.
- Ensure compliance by their workforce.
- Perform risk analysis as part of their security management processes.
The Breach Notification Rule requires covered entities and their business associates to provide notification following a breach of unsecured protected health information.
Is Piwik PRO HIPAA-certified?
Piwik PRO successfully passed a HIPAA compliance assessment as part of its SOC-2 Type II audit. This means Piwik PRO is HIPAA certified.
HIPAA certification proves that Piwik PRO Analytics Suite is a verified solution for customers whose policies mandate partnering exclusively with HIPAA-compliant vendors. This certification demonstrates our commitment to ensuring a HIPAA-compliant analytics suite safeguarding Protected Health Information (PHI).
How can you ensure your analytics is HIPAA-compliant?
You must apply a few safeguarding practices while collecting and processing data online. Some requirements you must fulfill include:
- Establish a business associate agreement (BAA) with every platform you use for marketing, advertising, and analytics and any other business associate. Otherwise, you cannot disclose PHI to that vendor without the individuals’ authorization.
- Address the use of analytics and other data platforms in your risk analysis and management processes.
- Implement administrative, physical, and technical safeguards – such as encrypting PHI transmitted to the analytics vendor and enabling and using appropriate authentication, access, encryption, and audit controls when accessing PHI maintained in the analytics platform infrastructure.
- Work with vendors that support values such as privacy by design to fully control and understand what data you collect, store, and transfer.
- Remove all 18 identifiers from PHI. Once the data is impossible to trace back to one individual, it is no longer PHI and no longer has protection under HIPAA.
Note: De-identification of PHI is not necessary with Piwik PRO – you can sign a BAA and send the desired PHI.
You need to carefully select an analytics vendor that would allow you to achieve HIPAA compliance – for example, don’t forget that Google Analytics is not HIPAA compliant.
You must either make an extra effort to avoid passing any trace of PHI to your analytics or switch to an analytics platform that will help you process patient data with the proper safeguards.
From safer data collection to real marketing results
Modern healthcare marketers deserve tools that don’t hold them back – track more, act smarter, and never worry about privacy compliance.