Webinar on-demand
A practical guide to digital analytics and advertising under HIPAA
In December 2022, the US Department of Health and Human Services (HHS) Office for Civil Rights (OCR) issued guidance on online tracking technology to HIPAA-covered entities. The bulletin details healthcare companies’ use of third-party cookies, pixels and other tracking technologies and elaborates on the definition of protected health information (PHI) that HIPAA refers to.
HHS’s bulletin emerged in the wake of numerous class-action lawsuits alleging improper disclosure of patient information filed against major health systems and hospitals. The bulletin urges HIPAA-covered entities to evaluate how they use online tracking technologies.
This article will examine how HIPAA-covered entities can follow HHS’s guidance and their options for HIPAA-compliant and effective approaches to analytics.
In November 2023, the American Hospital Association (AHA) sued HHS for its bulletin. Although a US district court ruled in favor of AHA, the issue of protecting PHI while using analytics tools remains unresolved.
Learn more: The AHA’s lawsuit against HHS guidance on online tracking technologies: What it means for HIPAA-covered entities and their use of analytics
The guidance on tracking technologies and its impact on your analytics
HHS guidance defines tracking technology as “a script or code on a website or mobile app used to gather information about users as they interact with the website or mobile app.” Examples include cookies, web beacons or tracking pixels, session replay scripts, and fingerprinting scripts.
The guidance explains that regulated entities disclose various pieces of information to tracking technology vendors through tracking technologies placed on their websites or mobile apps. Some of this data may include individually identifiable health information (IIHI), like someone’s:
- Medical record number
- Home or email address
- Dates of appointments
- IP address or geographic location
- Medical device IDs
- Any other unique identifying code
Healthcare information collected on a regulated entity’s website or app generally is considered PHI even if:
- The individual does not have an existing relationship with the regulated entity, and
- Data such as IP address or geographic location does not include specific treatment or billing information like dates and types of healthcare services.
The original version of the OCR bulletin assumed that anyone visiting a covered healthcare provider’s website was, is, or will be a patient of the provider.
The update to the bulletin from March 2024 states that the mere fact of matching identifying information, like a user’s IP address, with a visit to a webpage addressing specific health conditions or listing healthcare providers is not sufficient to constitute individually identifiable health information (IIHI) if the visit to the webpage is not related to an individual’s past, present, or future health, health care, or payment for health care.
The OCR’s bulletin also clarifies what parts of a website or app can contain PHI:
- User-authenticated webpages are pages that require users to log in. They often contain PHI in the form of an individual’s IP address, medical record number, home or email address, dates of appointments, diagnosis, treatment or prescription information, etc.
- Unauthenticated webpages are pages that don’t require users to log in. They contain general information about the regulated entity like their location, visiting hours, employment opportunities, or policies and procedures. Tracking technologies on many unauthenticated webpages do not have access to individuals’ PHI, in which cases they are not regulated by HIPAA.
Examples of situations where PHI is not disclosed include:
- Collection and transmission to a tracking technology vendor of a user’s IP address or other identifying information related to the user’s visit to a regulated entity’s job postings or visiting hours webpages.
- Collection and transmission to a tracking technology vendor of identifying information on a student who visited a regulated entity’s webpage to review its oncology service offerings for a research paper – here, such information is not related to the student’s health care.
On the other hand, PHI disclosures may occur in the following scenarios:
- Collection and transmission to a tracking technology vendor of an IP address, geographic location, or other identifying information on an individual who visited the same oncology webpage as mentioned above to seek a second opinion on a cancer diagnosis – here, it relates to the individual’s past, present, and/or future health.
- Collection and transmission to a tracking technology vendor of identifying information, such as an email address, on appointment scheduling pages and symptom-checker tools.
The examples provided by the OCR indicate that regulated entities should consider the intent of a website visitor in determining whether identifiable information is PHI and whether the specified disclosure falls under HIPAA. However, the updated guidance does not clarify how a regulated entity may determine a webpage visitor’s underlying intentions. In its brief, HHS seems to take the position that, if a covered entity cannot determine the intentions, the covered entity should err on the side of treating the information as if it is PHI.
- Mobile apps contain PHI provided by app users and their devices, such as fingerprints, network location, geolocation, device ID, or advertising ID. The updated guidance provides the following example:
- A patient may be using a health clinic’s diabetes management mobile app to track health information, such as glucose levels. The transmission of such patient’s information to a tracking technology vendor would be a disclosure of PHI because the patient’s use of the app is related to a health condition and is coupled with PII (for example., name, IP address, device ID).
Exceptions include information that users voluntarily download or enter into apps that are not developed or offered by or on behalf of covered entities.
AHA’s lawsuit against HHS bulletin and its impact on healthcare organizations
In November 2023, the American Hospital Association (AHA) filed a lawsuit against HHS for its guidance on tracking technologies. The AHA challenged the OCR’s interpretation of HIPAA, especially its alleged overly broad definition of PHI. The AHA stated that by limiting tracking technologies on sites, essential website tools like analytics platforms will no longer appear on hospital websites. This ultimately harms the patients that the OCR rule seeks to protect.
The AHA’s lawsuit was supported by 17 state hospital associations and 30 hospitals and health systems. In response to the litigation, the HHS updated its guidance on March 18, 2024, aiming to improve clarity for regulated entities and the public. However, the AHA called the modifications “cosmetic” and stated that “the modified Bulletin suffers from the same basic substantive and procedural defects as the original one.” In June 2024, a judge ruled in favor of the AHA, declaring that OCR had overstepped its authority when issuing the guidance. On August 29, the OCR decided not to appeal the district court’s decision.
The court ruling and HHS’ decision not to appeal it do not mean that the issue of protecting PHI in the context of analytical tools has been settled once and for all. The ruling was issued in a specific case, indicating that an IP address combined with visit data from an unauthenticated web page does not constitute PHI. However, the ruling does not vacate other parts of the guidance, like those relating to authenticated pages such as patient portals. While the court’s verdict may serve as a benchmark for later decisions on possible HIPAA violations, the complexity of PHI protection and the multiplicity of contexts involved would dictate special caution.
The fundamental issues surrounding the collection and use of PHI by healthcare organizations remain unchanged. What is allowed under HIPAA concerning the use of tracking technologies like analytics platforms continues to be subject to interpretation. While the definitions of PHI and ePHI are well-established, the widespread use and interoperability of modern IT systems make it alarmingly easy for PHI to inadvertently leak into your website or app. Therefore, it’s wiser to stay on the safe side rather than rely on a gray-area interpretation of PHI that maintains the status quo.
To protect patient privacy and reduce the risk of hefty fines and loss of trust, organizations must remain vigilant about the data they collect and share with analytics vendors. Notably, the biggest web analytics providers, Adobe and Google, have not changed their guidelines relating to the use of their most popular products: Adobe Analytics and Google Analytics 4. Those products should not be used by healthcare providers. Instead, they should seek out alternative solutions that prioritize data privacy and security. Their focus will likely shift towards analytics platforms that explicitly support HIPAA compliance and provide appropriate safeguards for handling sensitive health information, such as signing a business associate agreement (BAA).
How healthcare organizations can comply with HIPAA and HHS guidance
HIPAA-covered entities must:
- Disclose the use of tracking technologies in their website or app’s privacy policy, terms and conditions, and others. The passing of PHI to vendors cannot be based solely on such notices.
- Sign a business associate agreement (BAA) with a tracking technology vendor that meets the definition of a business associate before PHI is passed to the vendor. If a covered entity does not want to create a business associate relationship with the vendor or the vendor will not provide a satisfactory BAA, the entity must obtain an individual’s HIPAA-compliant authorization before disclosing PHI to a vendor.
Tracking technology vendors like Google Analytics are business associates if they create, receive, maintain, or transmit PHI on behalf of a covered entity for a regulated function, like healthcare operations, or to provide certain services to or for a covered entity (or another business associate) that involve the disclosure of PHI.
- Ensure that all disclosures of PHI to tracking technology vendors are permitted by HIPAA. Only the minimum necessary PHI should be shared for the intended purpose.
- Address the use of tracking technologies in their risk analysis and risk management processes. Implement appropriate administrative, physical, and technical safeguards (such as encryption and access, authentication, and audit controls) when they access ePHI stored in the tracking technology vendor’s infrastructure. These controls ensure that ePHI is protected from unauthorized access.
- Provide breach notifications to affected individuals, the Secretary, and the media (when applicable) when PHI is disclosed to a tracking technology vendor in a manner that breaches HIPAA requirements.
Healthcare organizations must inspect the tracking technologies they use, what tools can access PHI and whether they have BAAs in place, seeking out alternative solutions that prioritize data privacy and security. The focus will likely shift towards analytics platforms that explicitly support HIPAA compliance and provide the necessary safeguards for handling sensitive health information.
Your best bet is to find an analytics vendor that will sign a BAA and help you protect PHI on your website. What options do you have?
How to make your analytics HIPAA-compliant
Analytics platforms differ in their approaches to HIPAA compliance and some are more optimal than others. Below, we list the most popular options and explain their pros and cons.
Google Analytics 4 (GA4)
Google Analytics 4 (GA4) remains the most popular analytics solution, so many companies might view it as the default option. However, the use of GA4 by HIPAA-covered entities puts them at serious risk of security breaches and loss of patient trust.
Crucially, Google doesn’t permit customers subject to HIPAA to use Google Analytics 4:
“Customers who are subject to HIPAA must not use Google Analytics in any way that implicates Google’s access to, or collection of, PHI, and may only use Google Analytics on pages that are not HIPAA-covered.”
If you send any trace of PHI/ePHI to GA4, you’re violating both HIPAA regulations and Google’s terms of service, which can lead to the termination of your GA account.
Moreover, you won’t be able to sign a BAA for Google Analytics. Google is also open about using tracked data for its own purposes. They apply the data to develop new services, measure advertising effectiveness, and personalize content and ads. Using any PHI/ePHI for marketing or advertising without a BAA can be a serious violation of HIPAA.
And that’s not all. Google doesn’t offer choices for data residency, meaning all the collected data is stored in randomly assigned data centers both within and outside the US. As a result, you don’t know the location of your patients’ data, which HIPAA considers a breach of accountability.
You will need to configure your tag manager or customer data platform (CDP) before sending the data to GA4. Or you can de-identify all PHI. Such data is deprived of identifiers, so it is no longer viewed as PHI, which puts it out of HIPAA’s scope. Of course, de-identified data has its downsides, as it lacks valuable information needed to make your marketing campaigns more effective.
Let’s not forget that the limitations concerning HIPAA don’t end at GA4 or Google Tag Manager. GA4 is often used as a collection tool from which data is passed into a data warehouse or BI tool. Consequently, adding GA4 to your analytics stack damages your whole setup.
Given Google’s approach to PHI and the strict rules set out by HIPAA, using GA4 by HIPAA-regulated entities remains a risky endeavor. It requires ongoing attention and careful maintenance to ensure no PHI finds its way to Google’s platform.
Pros:
- Lots of talent on the market with experience and knowledge about using GA4.
- You can maintain your GA4 setup and the investment of time and resources into the platform.
- You get the flexibility of your own data warehouse.
Cons:
- Requires lots of maintenance and technical resources.
- PHI must be de-identified before being shared with Google – the process is time-consuming and error-prone.
- Sharing PHI with Google may result in HIPAA breaches and the termination of your GA account.
- Google uses the collected data for its own purposes.
An on-premises analytics platform
On-premises analytics refers to deploying and managing analytics infrastructure within an organization’s own physical location or data center. With on-premises hosting, the tracking technology vendor cannot access your infrastructure. The vendor isn’t considered your business associate, so you won’t have to sign a BAA.
Examples of analytics platforms that offer on-premises hosting include Matomo, Snowplow or Countly.
To be HIPAA-compliant, you must follow specific practices to build and maintain your on-premises infrastructure. For example, ensure your infrastructure includes:
- Data backups and recovery options
- Audit and change logs for your data and users
- Secure encryption of data at rest and in transit
Organizations get complete control over the data and flexibility to configure the infrastructure to their requirements. However, on-premises hosting is also costly to maintain and difficult to scale. Whether this option is viable depends on your organization’s needs, budget constraints, and strategic priorities.
Some organizations may opt for a hybrid approach that combines on-premises and cloud solutions to balance control and flexibility, such as the dedicated database – a private cloud offered by Piwik PRO.
Pros:
- Control over the data and what happens with it.
- You can adjust the setup to your company’s needs.
Cons:
- High costs.
- Requires maintenance and resources.
- The organization is responsible for failures and security incidents.
An analytics setup using a variety of tools from different vendors
More technical organizations can build their analytics setup with a few HIPAA-compliant tools. However, this approach can get complex. You need to evaluate your needs, understand what each tool offers, and check how it can help you comply with HIPAA.
Let’s look at an example of an analytics setup centered around Freshpaint as a data collection tool.
The HHS’s updated guidance clarifies that if the tracking technology vendor will not sign a BAA, a HIPAA-regulated entity could establish a BAA with another vendor, such as a Customer Data Platform vendor that could de-identify the online tracking information constituting PHI and then provide the de-identified data to the tracking technology vendor.
Freshpaint
Freshpaint is a data platform that connects customer data from the site or app to marketing and analytics tools through pre-built connections with the most common products. They’ve recently launched the Healthcare Privacy Platform, which is meant to safeguard patient privacy and make marketing stacks HIPAA-compliant.
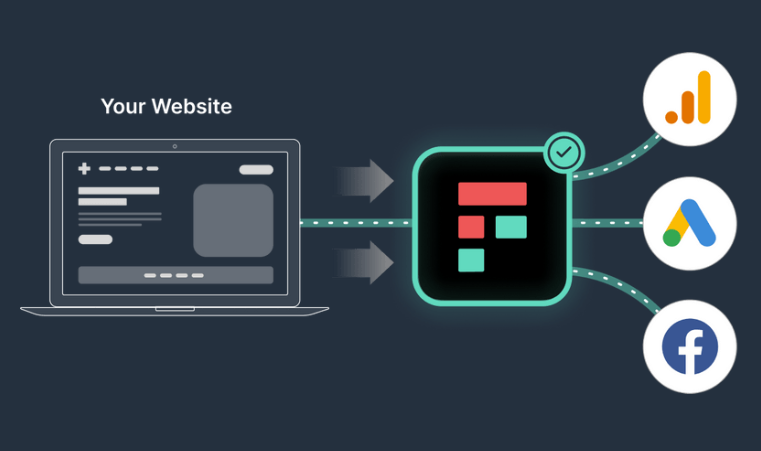
Freshpaint works as a layer between a website and other systems. It requires additional tools to make your analytics setup complete, such as a data warehouse and data visualization tool. You can also integrate it with analytics platforms like GA4.
Aside from signing a BAA, Freshpaint offers other dedicated HIPAA-compliant features:
- Allow List is an opt-in functionality that allows healthcare marketers to control what data is sent to a given destination.
- Event Verification lets companies see what information is being collected and sent to third-party tracking tools.
- Web Tracker Monitoring provides reporting on website trackers.
These features make Freshpaint’s offering unique, but it does have a fair share of issues.
Freshpaint’s limitations
Freshpaint is only a middleman – it takes in data, cleans it, and then sends it to a specific destination. You can’t report on or visualize the data within the platform. And while it helps you control and restrict the flow of PHI to non-HIPAA-compliant apps and systems, you can’t access and act on PHI within Freshpaint either.
You can use many analytics and marketing tools without identifying information, but this might restrict some of their capabilities. For example, if you exclude some events or URLs from flowing to GA4, your dataset will be missing data and won’t be fully accurate. If you reset visitor IDs or mask IP addresses, it will impact visitor stitching and customer journey analysis.
The bottom line is that Freshpaint lacks the use cases and features of analytics platforms. The setup and maintenance require significant technical skills, resources, and coordination across multiple teams. This also makes using the tool very costly.
Adjusting the platform’s settings requires understanding what metadata and properties are collected by a destination and whether they contain personally identifiable information (PII) or health information that could be viewed as PHI.
If you need to connect Freshpaint to a tool it doesn’t have an integration for, you must create it yourself. Depending on the tool, the process may require a lot of effort and you will have to overcome many technical hurdles to make it happen. And if you want to connect Freshpaint to an analytics platform that’s already HIPAA-compliant, you’re just adding an extra step.
Using Freshpaint with GA4
You can also connect Freshpaint to GA4 to strip any PHI from data before sending it to GA4, but your analytics will lack many identifying pieces of information.
The question remains whether GA4 is an optimal analytics platform for your needs beyond simply complying with HIPAA. GA4 has many limitations that vary in degree and affect companies differently. Despite recent improvements, GA4 comes with data sampling, configuration limits, insufficient privacy measures, complicated access to raw data, and missing features, to name a few.
If you’re struggling with GA4 and subject to HIPAA, it’s time to explore alternatives. By considering an all-in-one analytics platform that implements appropriate security measures and is ready to sign a BAA, you’re getting the best of both worlds: comprehensive analytics features and HIPAA compliance.
Pros:
- Dedicated HIPAA-compliant features, including signing a BAA.
- The ability for HIPAA-compliant companies to use popular marketing and analytics tools.
- The ability to combine the benefits and features of each tool in the Freshpaint setup.
- Avoiding unanticipated switching costs and losing the investment into the existing technology stack.
Cons:
- The connection between systems may not be seamless – changes or API updates by vendors may break your setup.
- A data analyst or database expert is necessary to manage and maintain the systems and setups.
- Costs are very high – you must pay for implementation, licensing of multiple vendors, and maintenance.
- The setup process is complicated and requires an understanding of HIPAA’s provisions and each destination tool’s specifications.
An all-in-one analytics platform
You can choose a HIPAA-compliant web analytics platform that will provide you with all the resources to collect, analyze and activate data, on top of features that will help you achieve HIPAA compliance. You don’t need to create and maintain resource-heavy and costly setups, and it’s a viable solution for organizations of all sizes with less technical teams.
Examples of HIPAA-compliant analytics vendors include Mixpanel, Heap, Amplitude and Piwik PRO.
Piwik PRO
Piwik PRO provides analytics software for websites, apps, and digital products with comprehensive integration and activation capabilities. You can sign a BAA with Piwik PRO, meaning you’re free to send all types of PHI and ePHI to your analytics setup. You don’t have to de-identify PHI or restrict its flow to analytics.
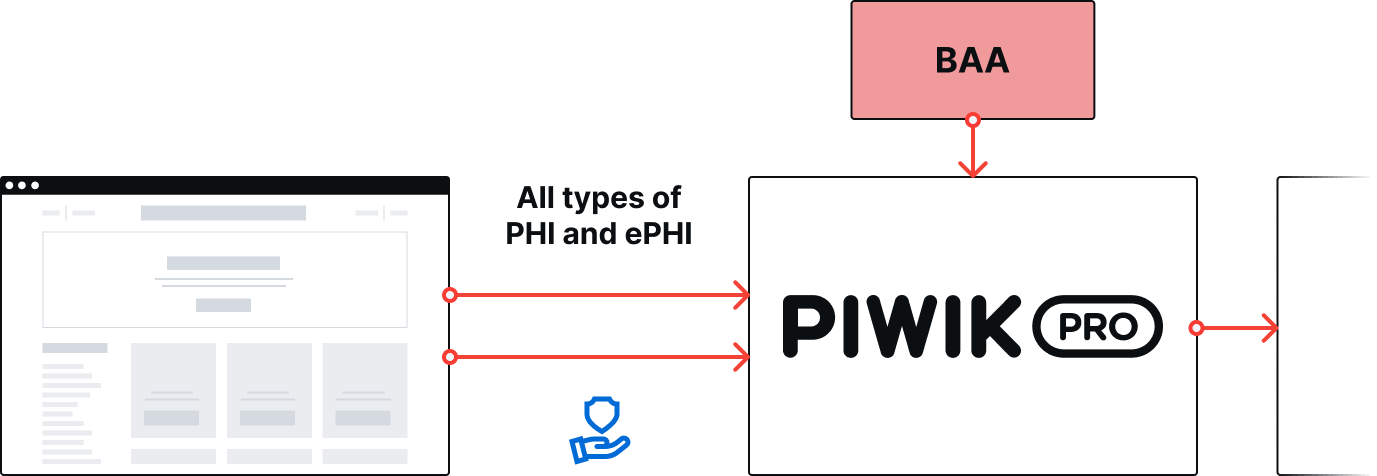
With Piwik PRO Analytics, Tag Manager and Customer Data Platform, you can safely collect and analyze PHI and ePHI throughout the whole customer journey and activate the data to improve patient experience.
Read more: Piwik PRO is officially HIPAA-certified!
You can also connect the suite of products with a data warehouse via scheduled raw data exports or API to expand the platform’s data analysis functionalities.
Additionally, you can achieve HIPAA compliance through other features, such as:
- Hosting on HIPAA-compliant Microsoft Azure data centers
- Ability to fully switch off the collection and storage of visitors’ IP addresses
- Encryption of ePHI when the data is at rest and in transit
- Advanced user-permission options to manage who on your team can access PHI
- Safe backup storage with maximum recovery capability
- Not sharing ePHI with third parties or reusing it for other purposes
- ISO 27001 and SOC 2 type II certifications and regular privacy and security audits
Learn how different analytics platforms approach HIPAA compliance: A review of HIPAA-compliant analytics platforms.
Pros:
- You can sign a BAA.
- You get an all-in-one platform with complete features and capabilities.
- Allows you to collect and use both PHI and de-identified health information.
- The vendor implements multiple high-level privacy and security features.
- Low cost.
Cons:
- You are using tools from one vendor only.
The bottom line
The HHS guidance on tracking technologies and other recent HIPAA developments give healthcare organizations little room for error on HIPAA compliance. Healthcare providers must remain alert to changes in the digital health industry as regulations and technology are continually evolving.
Above all, they should evaluate their analytics setup and understand their options for achieving HIPAA compliance. If the chosen vendor falls short of the requisite standards, they must be ready to pivot to a partner that meets their analytics needs and prioritizes compliance to avoid damaging breaches.










