It is easy to get paranoid about online privacy as there’s been a lot going on recently.
Max Schrems complaining about Facebook privacy abuse, allegations about the NSA peaking at everything you do, and the FBI-Apple encryption dispute are just a few examples. With the progress of technology the problem is growing bigger.
One thing is to know your rights as an Internet user. The other thing is to know how to actually enhance protection of your privacy. There will always be someone snooping on your data and looking for a way to get around the law, so you need to know how to protect yourself ahead of time.
We’ve discussed Safe Harbor, General Data Protection Regulation, Log Analytics, and many other subjects relevant from organizations’ point of view. But what about us?
- Am I safe when I log into my accounts from different devices?
- Who else can access my data?
- How can I be sure that I can trust all the people and companies I share my data with?
Answers to those questions might be quite blurry. But there is something that can be done to reduce risk and protect our digital privacy.
We’ve created a list of security measures to protect your digital identity and your data. Some of them may seem a bit extreme, but you can never be too careful when it comes to security.
1. Make smart decisions about where you place your data
It is really, really tempting to use the services offered by such giants as Google, Facebook, and Apple. The comfort they provide to users by merging various services into one account is a huge advantage. But everything comes with a price. In this particular case the currency you use to pay for better comfort and ease of usage is your data.
Let’s not forget what happened when iPhone creators stood up to the FBI in the shooting case in California. This incident transformed Apple into a guardian of users’ privacy. This is an unusual case which presents great user-centric approach. Not very common among large corporations. High-five Apple!
The point is, everyone wants your data as it drives the revenue of many companies. Cyber-criminals are constantly looking for security holes in software of all kinds. That’s one of the reasons why we are forced to install new updates so often. To reduce exposure to hackers’ efforts, you can switch to less popular solutions. For example, you can use Linux or Chromebook instead of Windows, LibreOffice instead of Microsoft Office, and Opera instead of Google Chrome. Or try Piwik PRO instead of Google Analytics 😉
Before you make any decision about transitioning from one provider to another, less common one, make sure the product you want to use is supported and updated on a regular basis.
Evaluate Your Web Analytics Solution Towards GDPR In 12 Steps
Find out if your analytics solution guarantees data accuracy and privacy, including GDPR compliance:
2. Take advantage of ad-blocking plugins.
There are countless automated crawlers waiting to learn how you use online shops, hotel booking sites, and bank applications. They collect your data even without your consent. This is all done to help them target their marketing efforts more effectively, which is a valuable practice from a company’s point of view. For you, on the other hand, it may lead to more spam in your inbox and to your data being shared without your permission.
There are hundreds of pieces of tracking software which can record your activity. Given that, it is possible that any of them can be hacked. Most web browsers allows you to add an ad-blocking plugin to restrict third-party cookies. For this purpose you can use a tool like Ghostery, or turn on incognito mode in your browser. Unfortunately, while incognito mode lets you avoid spammers, it is not a cure for all potential threats…
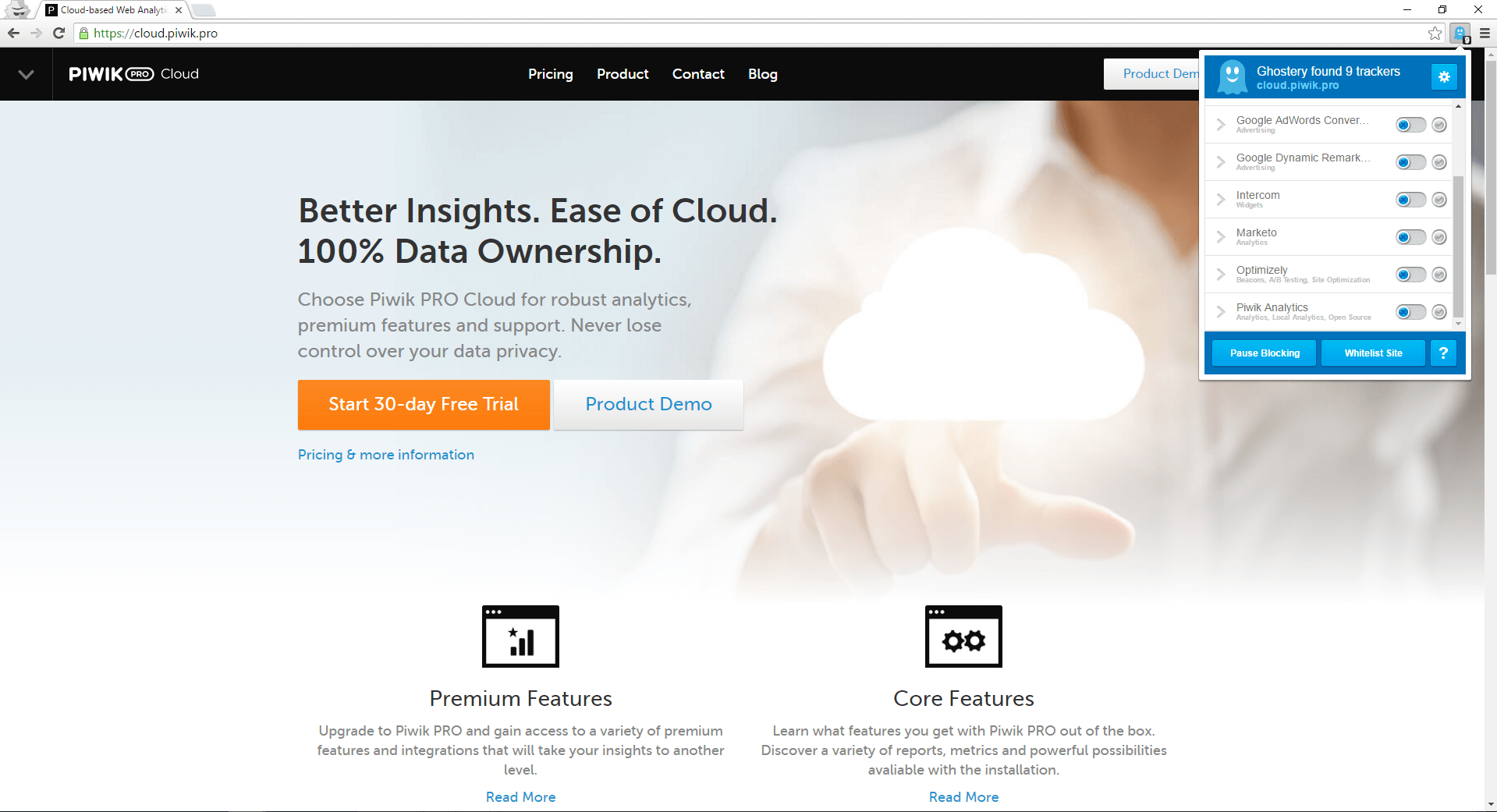
3. Use VPN when browsing the Internet
When browsing web the in incognito mode your history is not recorded. Moreover, after closing a window, all cookies collected during your activity are automatically removed.
This stops browsers like Chrome or Firefox from recording your data, but your router, operating system, and websites themselves will record data on your presence anyway. The alternative is to use a VPN (virtual private network). It secures your browsing data through encryption, ensuring that your browsing activity, download history, and even IP address is not shared with third parties.
Eric Geier, in his article How (and why) to set up a VPN today, explains that “if you’re concerned about your online privacy, connecting to an encrypted VPN while you’re on a public or untrusted network – such as a Wi-Fi hotspot in a hotel or coffee shop – is a smart, simple security practice.” You can find practical advice on how to set up a VPN on your own inside the article.
4. Encrypt your emails
There are many reasons why you should assume your emails are not exclusively yours. One of the biggest causes for concern could be allegations that the NSA has been spying on Americans’ phone calls and internet activity. Or the fact that your messages go through several servers between you and the recipient. There will always be some snooping corporations, identity thieves, and opportunistic hackers, so it’s important to act fast.
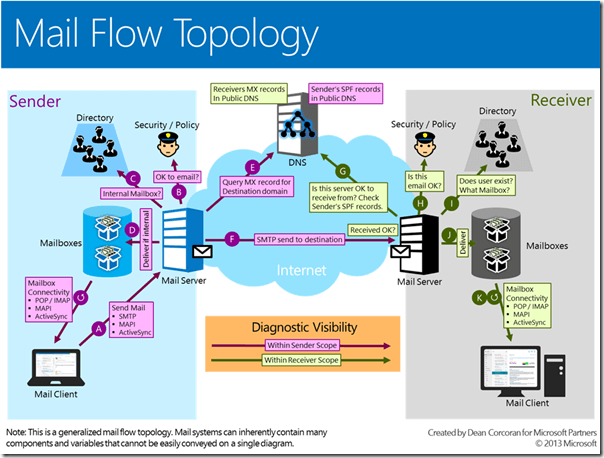
On the diagram below you can see what it takes to get an email from “here” to “there”. It was created by Dean Corcoran for Microsoft Partners.
5. Strong password generators keep your passwords secure
The average user in 2015 had at least 90 accounts connected to one email account. Every new account means we set a new password. It often happens that we reuse the same one again and again, because it’s impossible to remember every single password without duplicating.
We probably don’t need to point out that keeping all your passwords in one file is not the best idea, right? An alternative solution is to use a password manager like Dashlane. It can organize all your passwords in one place and generate secure ones if you can’t come up with anything on your own. Here’s how Dashlane dashboard looks like:

If you frequently log in to public PCs you need a solution like KeePass. Experts recommend using portable apps and an encrypted database, and KeePass gives you just that.
6. Opt out from Ads Personalization
When you visit a website connected to any Google product (AdSense, AdWords, DoubleClick, Google Analytics…), various cookies may be sent to your browser from different places on the web. They do not have to be sent by Google itself, but by any other URL. This happens when a given service is connected to a Google product. This particular website can be the sender of a cookie.
It’s reasonable for you to be concerned about your privacy here. Data about your online activity, interests, or even the things you buy online are shared with one of the biggest corporations in the world. But there is a way out! You can go to Ads Settings and opt out of Ads Personalization. You will still see targeted ads based on some general aspects like geolocation and browser type, but it is a step in the right direction in enhancing your digital security.

What about the future of digital privacy?
Freedom and digital privacy should no longer be taken for granted. There is an urgent need to raise awareness among data subjects in order to promote and amplify consumers’ voices. More and more people are feeling uncomfortable about sharing their data with third parties, which is a good sign. We need to stay alert. Levels of trust are continually decreasing, and this is happening for a reason. We’re finally waking up to the potential consequences of our online activity.
What will the future bring? Probably more advanced legislation on digital privacy, along with a dynamic and innovative market for online privacy tools. But in the meantime, take whatever steps you can to protect yourself.
Evaluate Your Web Analytics Solution Towards GDPR In 12 Steps
Find out if your analytics solution guarantees data accuracy and privacy, including GDPR compliance:









