If you’re using analytics or other marketing platforms to process personal data, including sensitive data, you might be wondering how to make sure it’s properly protected against cyberattacks. Collecting data using privacy-friendly software deployed on secure servers is only one piece of the puzzle. There’s even more ways to protect your data collection, including employing a trusted execution environment (TEE). In this blog post, we’ll introduce you to this concept and present ways a TEE can improve the security of your data.
The different states of data and their vulnerability to cyberattacks
Data can exist in three states: in transit, at rest, and in use. Data actively moving from one location to another, e.g. across the internet or through a private network, is called data “in transit”. Data that is not moving from device to device is called “at rest,” and data being processed, updated, erased, accessed or read by a system is called “in use.” In a world where we’re storing and processing an ever-growing volume of sensitive information – from consumer details, credit card numbers to medical records – protecting sensitive data in all of its states is more critical than ever.
Whether your application is deployed on-premises, in the private cloud or in the public cloud, cryptography has been seen as the solution to protecting data in all states. Solutions such as encryption are now commonly used to safeguard both data in transit and at rest, and are increasingly recognized as an optimal method for protecting data in use. But because this type of data can be accessed by more users, it’s more vulnerable to attacks and exploits. Therefore, attackers have made it their main target.
The consequences of not protecting data in use has become apparent in several high-profile memory scraping incidents, such as the Target breach, and CPU-side-channel attacks, which have dramatically increased attention to this third state. We could also observe high-profile attacks involving malware injection, such as the Triton attack and the Ukraine power grid attack.
Threats to data in use
What adds to the problem is that a potential attacker can use a couple of methods to get a hold of this data. They can either move from the software or network layer down to the firmware (“software down” approach) or from the hardware up to the firmware (“hardware up” approach).
In the “software down” exploitation vector, the attacker would typically exploit a vulnerability in the application code that would give them limited privileges on the host system. The attacker would then try to obtain full control over the host. In the final step of the system exploitation, the attacker would try to achieve persistence by deploying a backdoor on the host system or even in the firmware of various hardware components and, ultimately, during the booting (starting) process of the system.
In the “hardware up” approach, an attacker needs to have physical access to the host system. This type of attack is usually known as “evil maid”. In this class of exploitation vectors, the attacker would act through physical interfaces of the system, such as USB ports. Other vectors include tampering with hardware components of the host by disassembling the chassis.
Organizations looking to work with sensitive data must make sure that their data is protected against both “software down” and “hardware up” attacks. To do so, data must be kept safe throughout its entire lifecycle, or, in other words, in all the three states.
You might also like: What is PII, non-PII, and personal data?
How a trusted execution environment can protect data in use
A hardware-based trusted execution environment is a secure and isolated environment that prevents unauthorized access or modification of applications and data while they are in use.
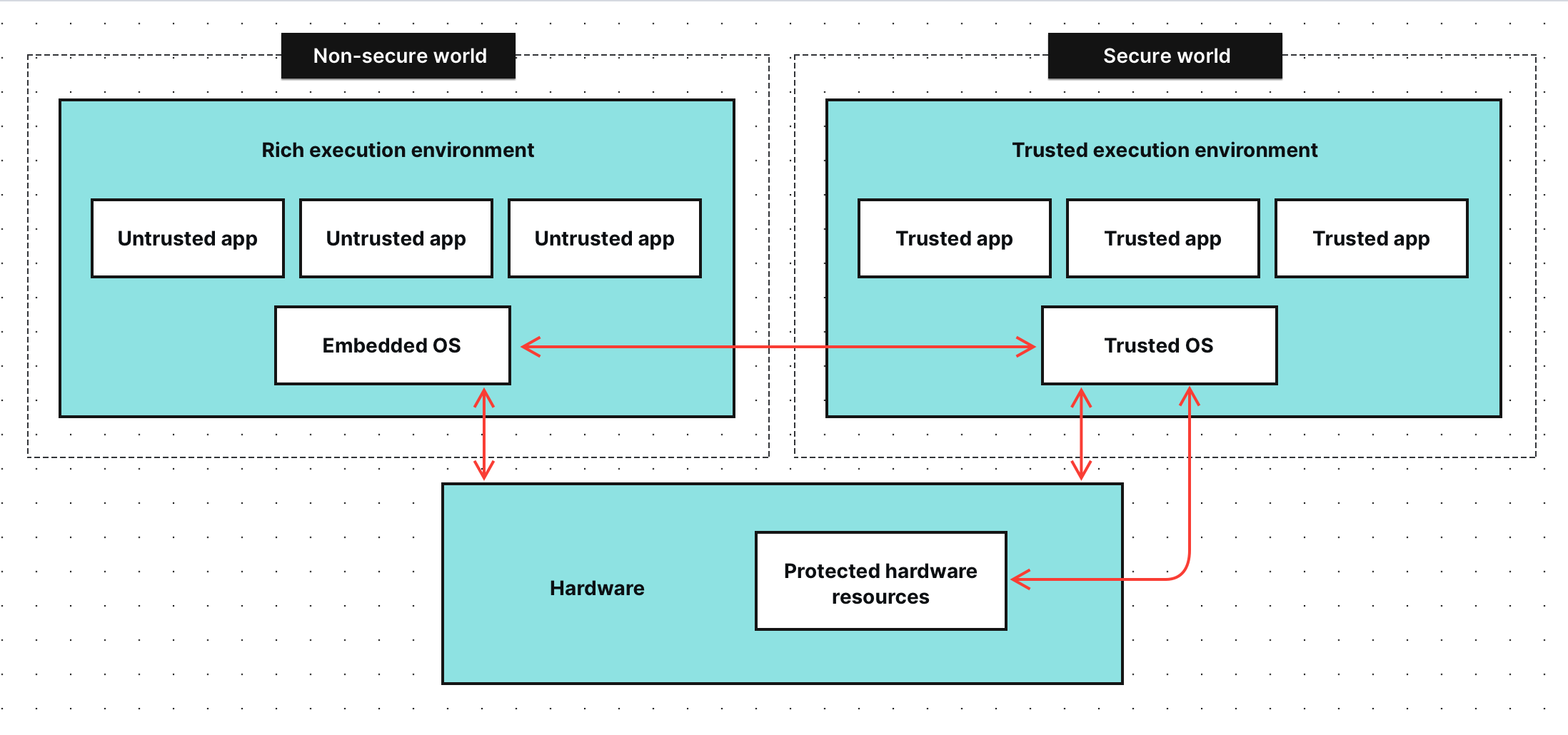
By that, it increases the security level of data in organizations that manage sensitive and regulated information.
A trusted execution environment (TEE) is a secure area of a main processor that guarantees optimal protection for highly sensitive data in all its states, with respect to confidentiality and integrity. TEE can be used on-premises, in the cloud or within embedded hardware platforms. For example, marketing analytics software processes sensitive data about clients and visitors and can keep such data safe during processing by deploying this application in a TEE.
An advanced TEE, such as CYSEC ARCA, manages to protect the entire stack. It guards against attacks from all angles, whether they are “software down” or “hardware up”. It also includes a built-in certified hardware crypto engine for key management and encryption. You can be sure that your data maintains its integrity and confidentiality, achieving compliance throughout its entire lifecycle.
The benefits of a trusted execution environment
Deploying an application inside a trusted execution environment protects data in use with confidential computing technology, without any changes in the application itself. In other words, it simplifies the process of adding a layer of security to an existing solution. Other benefits of deploying in a trusted execution environment include:
- Rapid deployment: Advanced TEE solutions are quick to deploy. Solutions like ARCA from CYSEC offer a rapid deployment of only 3 weeks for on-premises and 3 days for cloud – accelerating the go-to-market of organizations.
- Ensured data confidentiality and integrity: Ensuring the security of sensitive data in transit, in use, and at rest for critical applications and data.
- Secured deployment and execution of applications: By deploying inside a TEE, hostile applications are not able to exploit the operating system on which they run and cannot access the central processing unit (CPU) without explicit permission.
- Trusted Collaboration: A TEE is a safe environment for multiple parties to share and process their data. This opens up the possibility of using a TEE to securely collaborate with other organizations and individuals and get even more value out of your sensitive data.
- Simplified compliance: Achieve compliance with key management and encryption through an easy-to-use cryptographic API. Using a certified solution to encrypt or digitally sign sensitive data across the entire data encryption lifecycle: at rest, in transit and in use.
- Immediate return on investment: Inexpensive, rapid to deploy and easy to integrate and maintain.
- Weakest link protected: Access to data in use is blocked from unauthorized third-parties.
Conclusion
Sensitive user data is a powerful resource, but it has to be handled with proper care. This will help you comply with laws and build a successful relationship with clients who trust you with their data.
Failing to protect data in use can have dire consequences for companies looking to leverage sensitive data. These can range from experiencing business downtime to hefty fines resulting from failing to protect personal data.
One of the most effective ways for ensuring the safety of your data collection in all three states, both on-premises and in the cloud, is a trusted execution environment. It will add an extra layer of security to your data, and thus allow you to analyze your valuable analytics and marketing data with greater peace of mind.
Additional reading: