Evolving from a simple document to improve website usability, Cookies have become instrumental in how website users are tracked for advertisement purposes. While they’ve been used in advertising for a long time, digital privacy has recently become a global issue in which cookies play a big part.
In this post we cover how first-party, third-party and advertising cookies work, how to determine the status of them on your website and other sites, and the changing legal landscape.
Step 1: Brush up your knowledge
A cookie is a small text document that websites pass to your computer via your browser. Internet cookies have many functions like saving user input, login information, shopping carts, wish lists, analytics, advertising and more. They enhance and simplify the user experience when browsing a website.
Let’s look at the two most popular types of cookies:
- First-party cookie: Cookies created by the website (first-party) you’re currently viewing. For example, you visit www.xyz.com, and a cookie is saved on your computer from www.xyz.com with all your preferences for viewing this website.
- Third-party cookie: Cookies created by websites other than the one you’re visiting. For example, you visit www.qrs.com, the cookie from www.qrs.com is saved; again this is first-party. However, if www.qrs.com has an advertising banner from www.superads.com, this banner will also save a cookie. This is a third-party cookie: it does not originate from www.qrs.com (the website you’re visiting).
- Secure (HTTP only): Contains an “HttpOnly” flag that only allows the cookie to be accessed by websites using the HTTP/HTTPS protocol. This is a security measure to prevent Javascript access and XSS exploitation.
- Zombie: Use Flash cookies as a backup. Normally when you clear cookies from your browser that data is lost, and the collection process restarts when you visit that website again. With the zombie type cookie, a Flash cookie backup version is saved. When you visit this website again the Flash version is referenced and that data is used in the new HTTP cookie. The data is stored outside of the web browser and re-used whether browser cookies are deleted or not.
Read more about the differences between first and third-party cookies in this blog post:
First-Party vs Third-Party Cookies: Why First-Party Is the Way to Go
How third-party advertising cookies work
Most of the buzz you hear around cookies is related to those used for advertising. Normally, a website saves a cookie to remember your user preferences to be used the next time you visit to optimize your experience. In this way, it only benefits one user’s experience with one website.
Third-party cookies are different since they take information from a person who is visiting a different domain. Often this data is taken and shared without the user’s knowledge.
Information sharing
Cookies applied for advertising – almost always third-party – collect and share user data through vast networks about visitors from millions of websites.
To learn more details about information sharing by advertisers, check out this post.
Think of it like this:
There are three rooms connected by a corridor. In each there is one person (website).
These three people share the corridor, but there is no way for them to communicate with each other; they are essentially three information silos.
You enter room #1 and share some information: “Hello, my name is Peter.”
In room #2, you tell the person “I want to buy a BBQ grill.”
In a first-party type cookie relationship only room #1 knows your name, only room #2 knows that you want a BBQ grill, and room #3 doesn’t know anything because you haven’t been there yet. Each room (website) only knows what you have directly shared with them during your visit.
With first-party cookies, when entering room #3 you would hear “Hi, you’ve never been in my room before. How can I help you?” But in the third-party system you may be surprised when you enter room #3 and hear “Hello Peter, so what color would you like that grill in?” How do they get this information?
Among several other methods, advertising agencies use cookie syncing to share data collected across the web from multiple websites. Imagine it as a huge collaborative CRM where they dump all the info they gather about visitors.
Now let’s go back to our three rooms and the simplified CRM example. When you shared your name with room #1, it was automatically shared with rooms #2 and #3. And your interest in the BBQ Grill was passed to rooms #1 and #3.
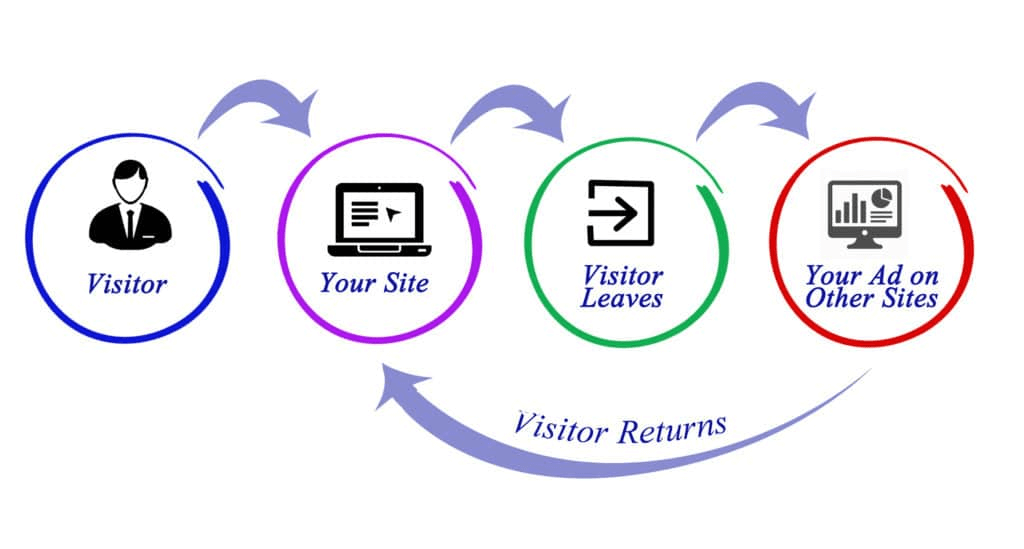
Cookie controversy and pushback
People began feeling uncomfortable when websites they were visiting for the first time displayed personalized advertisements. This inspired people to get informed and start asking questions about the technology that was tracking and targeting them across the web.
The demand for privacy-boosting tools like ad blockers, VPNs and improved web browsers has generated tons of cookie-killing technology. Apple’s Intelligent Tracking Prevention is a notable example of the industry recognizing the need to step in and offer solutions for concerned users.
Almost every mainstream web browser has followed Apple’s lead and now comes with a simple and sometimes automatic cookie management system that empowers users to take control. See what Google Chrome is doing about it.
But it’s not just tech companies who have responded to a privacy-conscious public. A lot of new government legislation has been created too…
Legal Regulations
Even if the General Data Protection Regulation and ePrivacy Regulation haven’t caught your attention in the news, you’ve definitely seen tons of messages with titles like “Changes to our privacy policy” in your inbox.
The European Union’s efforts to regulate data privacy have changed the landscape of the internet as we know it. But this isn’t happening only in Europe, and it’s not stopping.
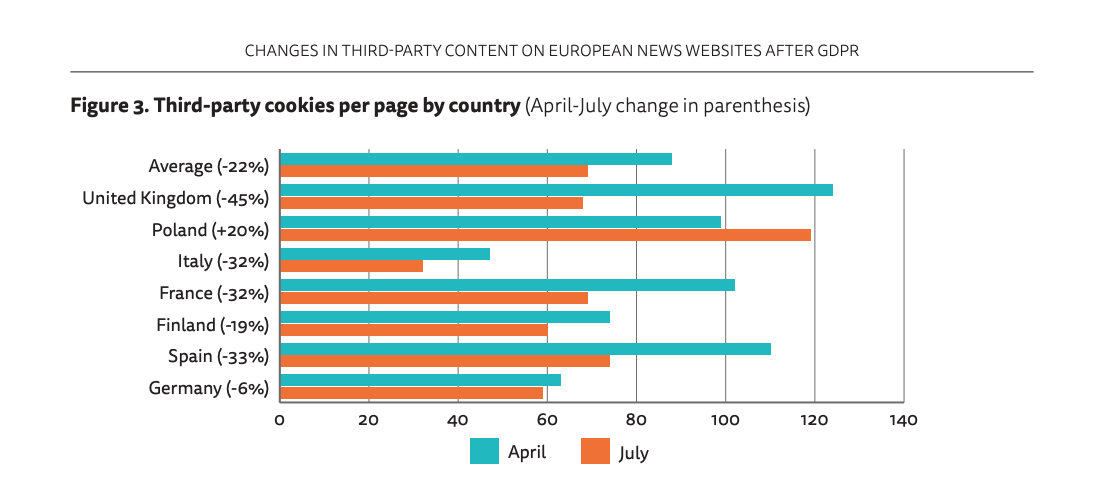
There has been a drop in the use of third-party cookies across the EU, but as this report titled “The State of GDPR Consent” shows, many websites are still not in compliance with GDPR.
There’s plenty of tools available to help organizations meet today’s privacy expectations. Nevertheless, so many of them still don’t realize their use of third-party cookies without consent is illegal.
Consent management platforms, for example, which prompt website visitors to provide consent to set cookies, simply didn’t exist before privacy regulations like GDPR came about.
There are other regulations besides GDPR that you should know about. Here are some of the most important:
Vermont Act 171 of 2018 Data Broker Regulation
The new law from this USA state regulates the activities of brokers. Beginning this year, data brokers – businesses that collect and sell data on individuals they don’t have a direct relationship with – must register themselves with the Vermont Secretary of State on an annual basis, comply with a long list of security requirements, and provide customers with a way to opt-out from the sale of their personal information.
California Consumer Privacy Act
In a nutshell, CCPA empowers residents of California to know the types of personal information businesses collect about them and gives them the right not to agree to the sale of their personal data to other parties.
Many people believe that GDPR inspired the CCPA. There’s some truth in that because they have a lot in common. However, unlike the European law, CCPA is more concerned with the sale of data than the collection and processing of it.
Brazilian General Data Protection Law (LGPD)
The Brazilian General Data Protection Law (LGPD) creates a new legal framework for the use of personal data in Brazil, both online and offline, in the private and public sectors. It’s important to note that the country already has more than 40 legal norms at the federal level, directly and indirectly, dealing with the protection of privacy and personal data.
The LGPD will replace and enhance these many frameworks, which were sometimes in conflict with one another.
India Personal Data Protection Bill
India’s new privacy law is one of the more controversial ones. Experts criticize the draft for its many shortcomings and disputable clauses. One of the most important is that the bill allows the processing of personal data in the interests of state security, if authorized.
Also, it permits the processing of personal data for the prevention, detection, investigation and prosecution of any offense or any other violation of the law. It poses an enormous threat to the right to privacy, considering the weak protections against state surveillance that exist in India.
Chile Privacy Bill Initiative
The new law amending the Chilean Constitution was published on June 16, 2018. It establishes the protection of personal data as a constitutional right. Through this amendment, personal data protection was established as an autonomous right. Here you can find the most important facts about the new Chilean law.
New Zealand Privacy Bill
New Zealand’s new Privacy Bill is set to replace the outdated Privacy Act that was passed 25 years ago. The new bill will implement recommendations from the Law Commission issued in 2011, and also would give more power to privacy commissioners.
The legal landscape for organizations handling individuals’ personal information is changing. It’s more important now than ever before to take stock and see where you stand both legally and ethically.
It’s clear that laws regulating the use of personal data are here to stay.
If you want to learn even more about these regulations head over to our blog post about privacy laws.
Step 2: Establish the goals of your cookie audit
You’re responsible for handling the data you gather from visitors to your website. Cookies pile up as your website gets more advanced, and it becomes harder and harder to keep track of what they’re doing.
Keep in mind your reasons for performing the audit: what do you plan to achieve?
Checking compliance with privacy regulations like GDPR, LGDP, etc.
Any business that collects data through their website from people in countries with data privacy regulations in place needs to verify their compliance with those regulations. If you don’t get consent before using third-party cookies to gather data, you can face huge penalties and an even bigger PR nightmare.
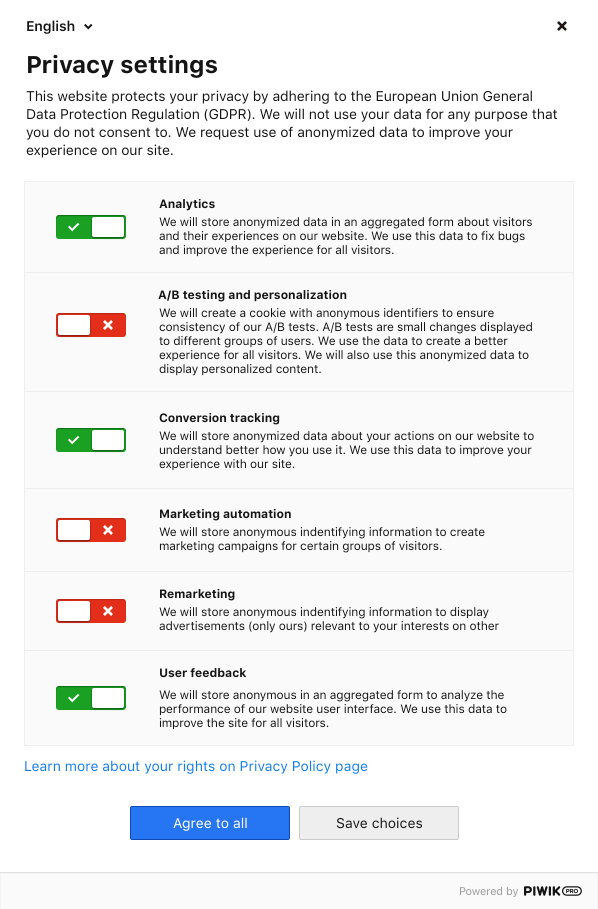
User consent is something that comes up often when discussing privacy regulations. To obtain satisfactory consent, the user must be made aware of the purpose of cookies and what type of information they collect. In addition to these details, the user must also be allowed to opt-in or out of using this cookie.
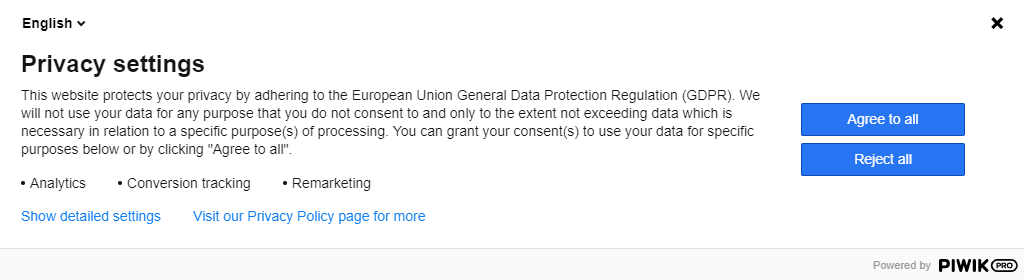
As you can see in the photo above, the user has the choice to opt-in or out of both analytics and remarketing cookies being used on the website. As required by GDPR, the purpose of data collection for each type of cookie is explained in a way that’s quick and easy to understand.
Checking compliance with internal privacy and security regulations
Internal regulations vary across industries. It’s common to find very strict policies among financial, healthcare and similar enterprises handling sensitive data. For example, banks need to pay special attention when managing post-login data collected by cookies. Such information should be encrypted and stored locally. It’s important to have control and ownership over sensitive data from secure areas.
Health and insurance organizations that fall under HIPAA regulations need to pay special attention to data processing/managing. Any cookies handling Protected Health Information (PHI) are risk factors that require appropriate security measures.
Validating potential data breach or leak threats
HTML cookies are exploited in all kinds of cyberattacks like cross-site scripting, session hijacking, DNS poisoning, etc. Measures must be taken to “harden” and encrypt cookies carrying sensitive data, especially session cookies that are frequently under attack from session hijacking attempts.
Updating privacy policies
When collecting data using cookies it’s important to adopt a privacy policy, both for compliance reasons as well as for transparency with your users. Cookie policies should include consent, disclosure and an opt-out option.
As more and more countries adopt data privacy laws, these policies are increasingly crucial. To create a GDPR-compliant cookie policy you will need to explain:
- Who is processing the data
- What legal basis allows you to collect user data
- What are the purposes of collecting personal data
- What types of personal data you collect
- How long you’re going to store the data
- Whether you transfer the data internationally
- Whether you use the data in automated decision-making
- What third parties you share the data with
- What are the data subjects’ rights
- How you’ll inform users that your policy has changed
Learn more about creating privacy policies from our post:
10 Elements Every GDPR-Compliant Privacy Policy Should Have
Step 3: Conduct the audit
The first step to establishing where you stand is to find out what cookies you’re setting. You’ll need a full list of cookies firing on your website to confirm they’re listed in your privacy policy. The most popular ways to do so are manually checking or using a scanner.
Manual check
If you choose to go the manual route, start by clearing the existing cookies (how to delete flash type included) in your browser before you start with the audit. Browser extensions like Ghostery and EditThisCookie are extremely helpful when conducting a manual audit. We suggest installing these tools before you begin.
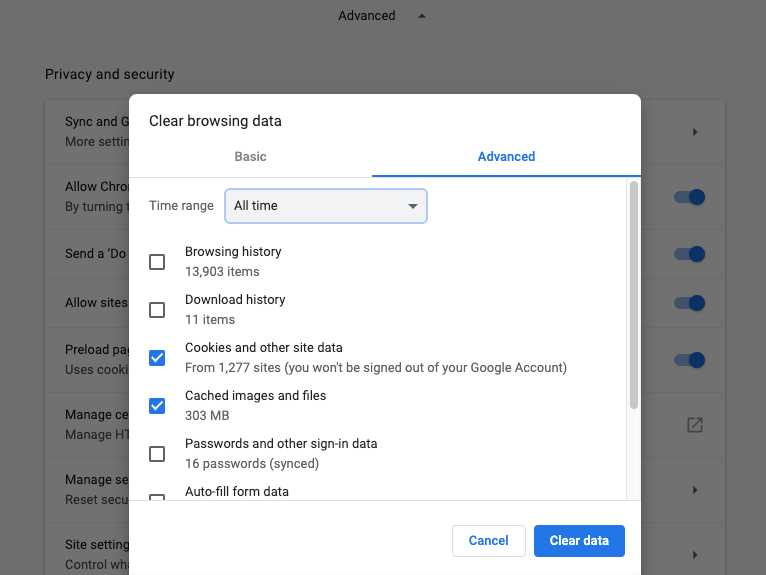
After you’ve cleared your cookies and have a “clean slate,” go to the website you want to verify and check which cookies are set via your browser.
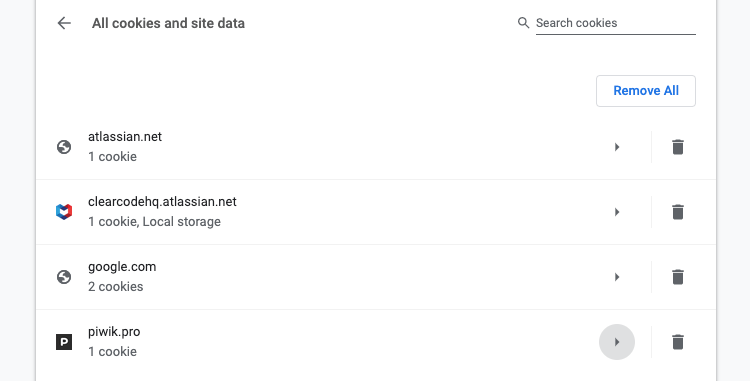
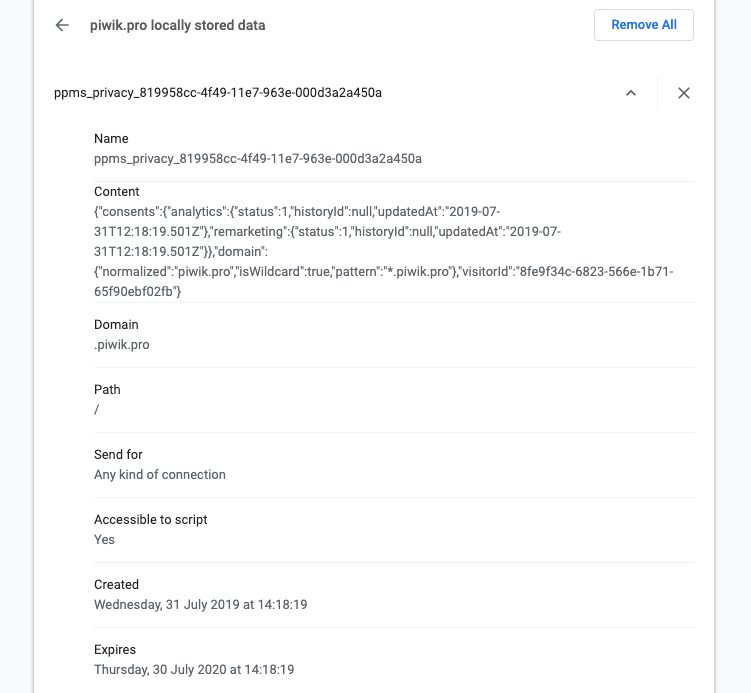
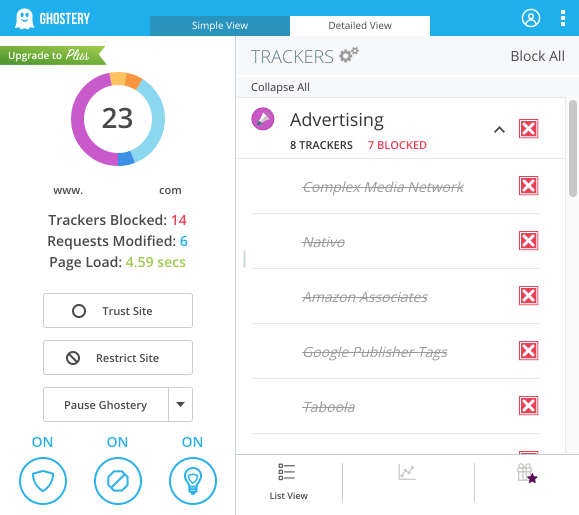
You can build a comprehensive list with this manual method, but it may take a long time depending on your cookie portfolio. It’s much quicker to use a scanner.
Cookie scanner
The second method for conducting a cookie audit involves using a cookie scanner. Let’s look at how Piwik PRO’s Cookie Scanner works:
Enter the URL (address) of the website you want to check and the email address you want the report sent to. The tool will gather information about all the cookies being set on that website and send the report to you.
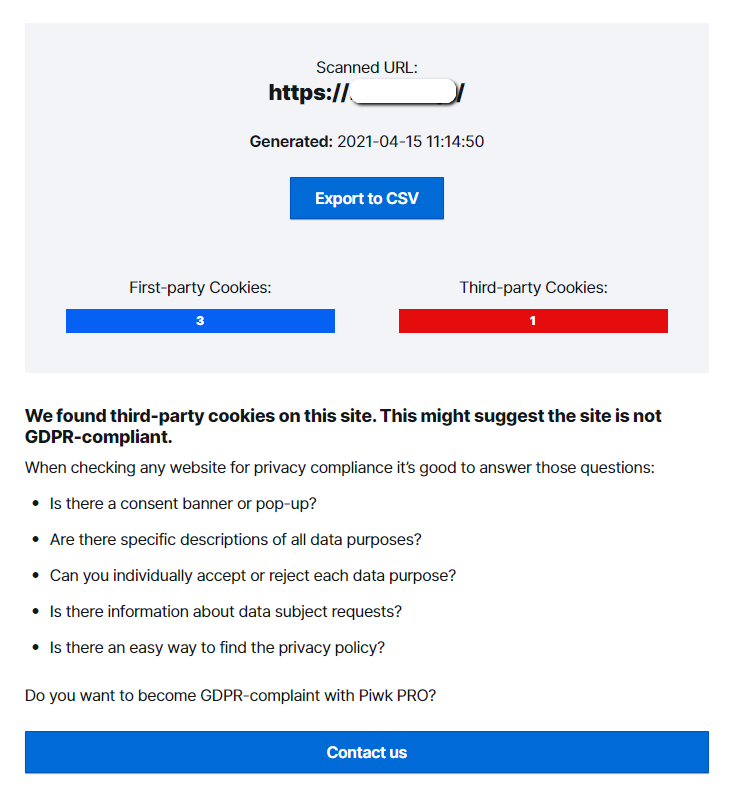
The report gives you a general idea of how many cookies the website is using and if any third-party cookies were found.
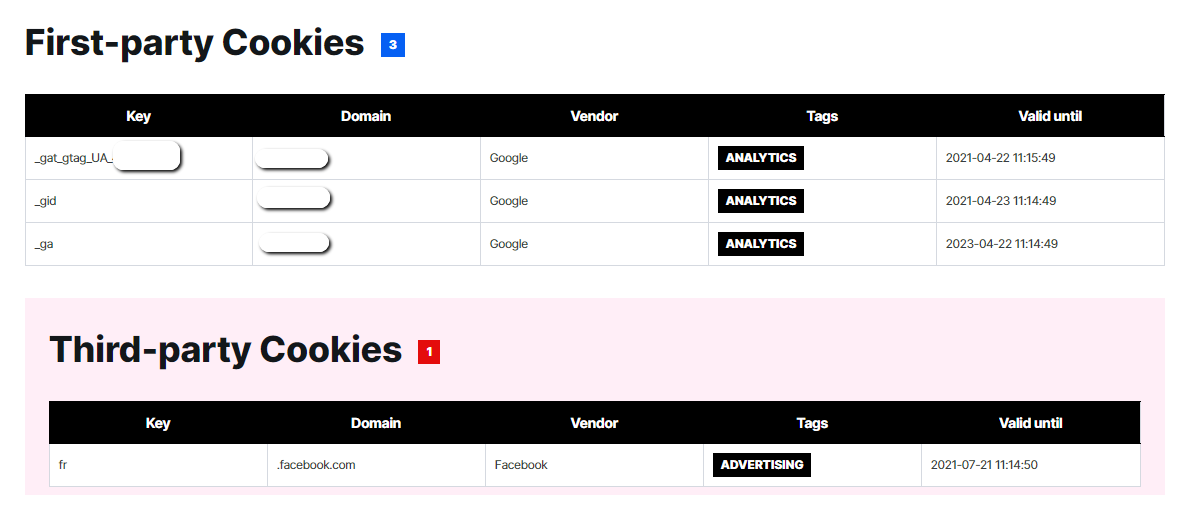
Important information about first-party and third-party cookies is included. Clicking on a specific key provides a detailed drop-down list.
Test out our tool and get your free report today
Piwik PRO Cookie Scanner
Step 4: Take action after the audit
Now that you know the situation on your website you can make some informed strategic decisions. Below are guidelines to help you formulate the general post-audit procedure.
Take a step back and ask yourself:
Are you familiar with the cookie’s vendor and information collected?
What do you need to know about cookie vendors?
- The credibility and reputation of a vendor can tell you a lot from the start. If your research is leading you to some bad reviews and shady info, you may reconsider your association with this vendor.
- You also should know what tools make this cookie function and how they work (PHP, JavaScript, Secure/HTTP Only, etc.).
- Other important details about vendors include how they store and process cookies and whether or not they offer a data processing agreement.
It’s important to distinguish which cookies are collecting sensitive information like personal and session data. Without knowing what cookies are collecting, you won’t be able to make decisions about legality, security, and privacy.
Is there a clear reason you’re collecting this information?
HTTP cookies are great tools for improving your website’s overall performance. They must have a specific task and purpose. There’s no benefit for you or your users to have random cookies collect data for reasons unknown.
GDPR states that data collection should be “adequate, relevant and not excessive in relation to the purposes for which they are collected and/or further processed.” This means data should not be collected without a clear motive or in excessive volumes.
An example of going overboard: Facebook’s “find my friends” feature takes contact information from your phone to use for ad retargeting; they’ve also used 2FA for harvesting mobile numbers for advertising. This is a clear case of stocking private data for monetary purposes.
Step 5: Identify red flags
Depending on the goal of your audit, you have to establish what findings will be marked as red flags. For example:
Cookies with no expiration date or with an exceptionally long expiration date, like 365 days
Most privacy regulations are rather high level, not granular. The ePrivacy regulation, on the other hand, contains specific information regarding cookies. According to ePrivacy, persistent cookies (the ones that don’t expire when you close a browser) should last no longer than 12 months. Following the 12-month expiration, rule not only keeps you compliant but also makes sense since there isn’t much use in tracking an inactive user for years.
Cookies that are installed without user consent
Your website should be set up so that no cookies are fired without consent. Any cookies bypassing this process need to be adjusted immediately. Make sure these renegades are listed in your privacy policy and consent banner, and they won’t fire until you get consent.
Check out this post to find out more about how consent managers work together with tag manager.
Integrate a consent management platform with your tag manager so cookies can’t fire before the user gives consent. With these two tools working together you’ll have a bulletproof consent solution.
Cookies that aren’t mentioned in your privacy policy
After you’ve put in the work to create a comprehensive privacy policy, go back and make sure you’re operating according to those guidelines. Now’s the time to do a side-by-side comparison of cookies found in the audit to those in your privacy policy. Any discrepancies need to be dealt with right away: either add them to the list or remove those that shouldn’t be there.
Cookies tracking user activity in data-sensitive areas like secure member areas, post-log-in areas, online banking, sign up forms collecting sensitive user information
Keeping sensitive user information safe is crucial. The problem with using cookies, especially the third-party kind, in sensitive areas is that you lose control over data as it is transferred to offsite entities. You may choose instead to log files or use first-party cookies for storing data within your infrastructure, as long as you maintain control of the data in the process.
What you don’t want is retargeting pixels like Google Ads, Doubleclick, Ad Form and other DSPs and Ad Networks gathering sensitive data and sending it via third-party channels you can’t track or secure. That would put users’ sensitive data at serious risk.
Conclusion
Organizations are fighting a privacy battle on two fronts. On the one hand, the general public’s knowledge and expectations are at an unprecedented high. On the other hand, legal regulations addressing privacy online are constantly popping up all over the globe and show no signs of slowing down.
We’re confident that our cookie scanner will show you where you stand. Remember, at Piwik PRO we’re always here to help you manage privacy and compliance issues for your website.











